6. Nov. 2020 by Markus
Retrospective Release 5.5 modernizes and improves SSH support
Soon Retrospective will celebrate its 10-year birthday :-) Since its inception it has helped a lot of people connect to servers and virtual machines using SSH.. The ability to quickly search and monitor data and a fully-featured SSH console have led our customers to collect tons of connections in Retrospective Host Manager and use Retrospective as their primary tool for SSH connections.
Even though IT workloads tend to move into containers, for which use case Retrospective was extended with Kubernetes and Docker connectivity a while ago, the SSH protocol still remains a cornerstone in our daily IT life.
In this blog I explain new the SSH features of the release 5.5: Ed25519 SSH signature schemes and SOCKS/HTTP proxy connections, along with related SSH connection functionality that was already present in earlier releases like jump servers and identity changes.
Ed25519 SSH signature scheme
Now Retrospective supports the new SSH signature scheme Ed25519, which was introduced recently. It is an EdDSA implementation that uses Twisted Edwards curve elliptic curve cryptography that is faster and more secure than DSA or EcdDSA. Even the widely used RSA algorithm is not considered safe anymore if it’s generated with the key smaller that 2048-bit length.
We expect major migrations to Ed25519 at all infrastructures globally, because the Ed25519 keys allow for very fast signing and significantly increase the security level. So it was important to incorporate Ed25519 into Retrospective.
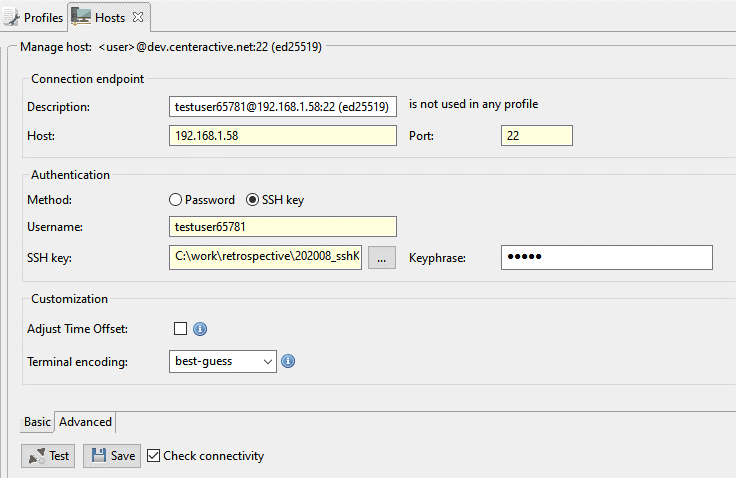
The SSH scheme is automatically recognized when you create an SSH connection with a user and its SSH private key to a target host, and the user has an Ed25519 public key configured on that host.
SSH connections through HTTP and SOCKS proxy
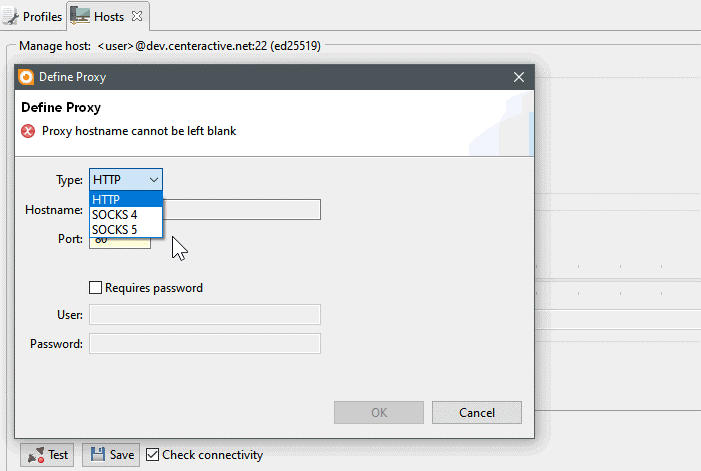
Customers have frequently asked to be able to make connections to remote servers and virtual machines through proxy servers, so we have provided this option in Retrospective 5.5.
A SOCKS proxy operates on a lower level than an HTTP proxy. It can even forward UDP traffic and work as a reverse proxy, whereas an HTTP proxy cannot. The HTTP proxy is working using the HTTP protocol and is therefore more limited. Routing connections through a proxy server, often acting as firewall, filter or demilitarized zone guard, can provide increased security. Some proxy servers also help caching data and balance traffic to different endpoints, thereby improving performance.
The Hosts configuration now allows for an easy proxy configuration, when you have to go through a proxy server to reach your target system with an SSH connection. The option is located on the Advanced tab of the Hosts panel.
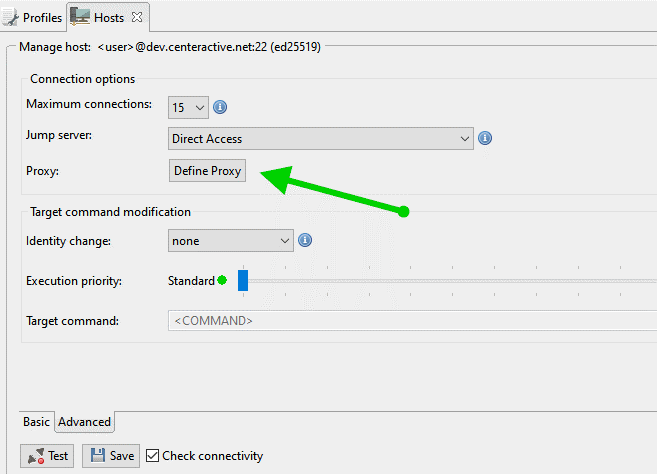
After entering the connection information for the proxy, Retrospective connects to a target host through the proxy.
Jump servers
Many administrators set up jump hosts as secure entry points to the workload hosts. Retrospective supports jumping with a connection over multiple hosts and so allows for the most sophisticated SSH connections. The jump server option as been implemented for quite a while, now this blog would be incomplete without mentioning it. The configuration is simple.
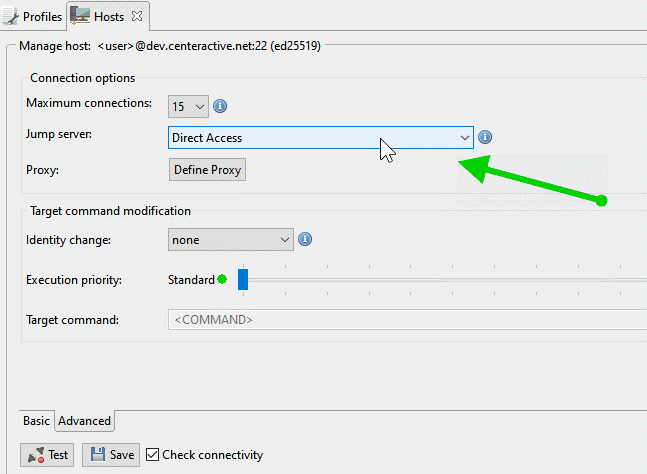
The jump host connection has to be configured and saved beforehand, then you can select it when you setup a new jumped connection.
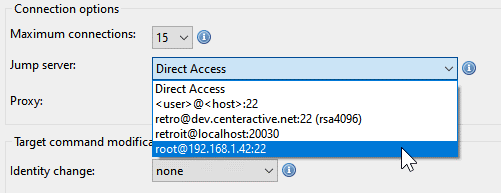
The jumped connection then indicates its jump route in the Hosts configuration panel.
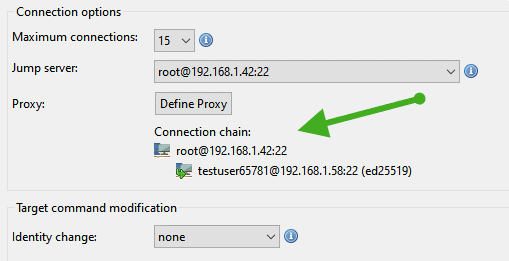
Identity changes
Even before the release of the jump server feature, Retrospective provided the ability to change your identity after the SSH connection has been established. We have learnt about a multitude of different kinds of user account settings amongst our customers, so it is crucial that Retrospective supports identity changes.
The user-id of an SSH connection can be changed with a sudo command. All commands issued by Retrospective will then subsequently be executed with that changed identity. The sudo command is present on all Unix-like systems, and allows users to run programs with the security privileges of another user. The identity change is also configured on the Advanced tab of the Hosts panel.
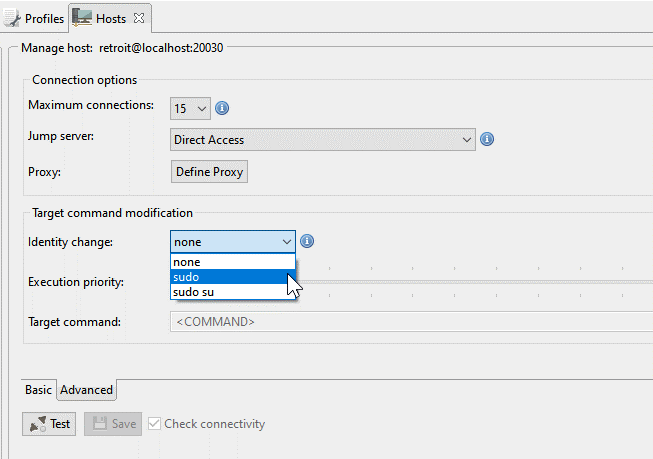
The sudo command is supported with or excluding the “su” command, which additionally enables you to switch to the super user, or rootuser.
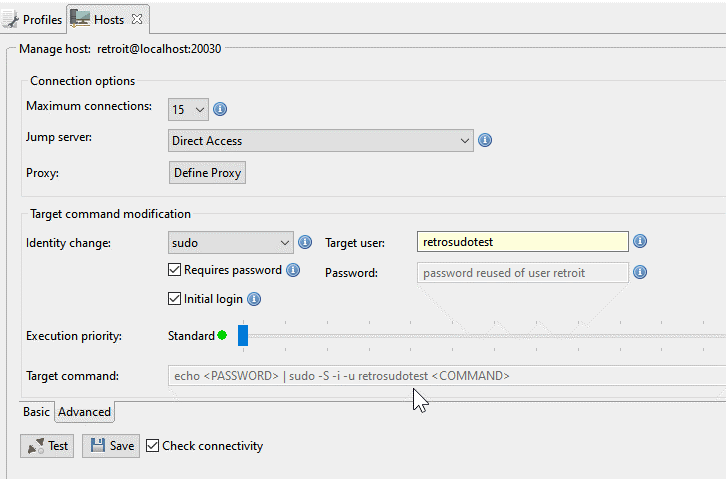
After entering the target user-id for the identity change, you can choose with two checkboxes if the password needs to be given and if you want a new initial shell for the target user. Retrospective will, after connecting with an identity change, execute all commands using the prefix stated in the Target command box (greyed out value).
So for example if you have a policy that allows certain logs files only to be read by a certain user, you are covered.
Final word
Retrospective helps you to organize the most demanding collections of SSH connections in a simple and efficient way. As opposed to other SSH tools it also simplifies the configuration of advanced connection techniques like proxies, jump hosts and identity changes.
Log file searching and monitoring via SSH is still executed with high speed, while at the same time economically using target server resources.
As usual, we also fixed a number of bugs and issues that were reported from our customers. We hope that the new Retrospective version 5.5 will help you even more than before to deal with the ever growing digital complexity we all face nowadays.