23. Aug. 2012 by Kevin
Retrospective features in a nutshell
As we have discussed in a previous paper, the industry consensus is that immature searching and reporting capabilities have become the bottleneck in current log management offerings. It is obvious that when you have hundreds of devices producing logs, no analyst has the time to analyze even a part of them, let alone identify the important events amidst such a flood of data. So, any improvements in the processes for querying logs and extracting pertinent data from them can only be welcomed. In response to this need, the latest version of Retrospective provides a basic type of automated log analysis. It does this by implementing a log analyzer that provides an easy-to-use friendly GUI with many useful search query and filtering features to help in the rapid detection of incidents currently occurring, or that have occurred in the recent past.
The Tail Feature
One of the most useful of these features is the Tail feature. Tailing is used to monitor changes to log files, detect any matches to the specified search parameters and display the entries containing the defined term in real-time. This makes Tail ideal for watching log files in real-time, enabling you to respond quickly to any critical events.
User Scenario
So, suppose you find something suspect in the logs of one of the devices on your network. The log contains warning messages and you want to keep an eye on this device, and maybe associated devices, without having to create specific, post-incident searches. What you would really like is to be able to monitor the logs of suspect devices for any new instances of this warning message, in real-time (just like expensive monitoring solutions but without the cost or complex setup). Retrospective’s tail feature is ideal for this scenario.
Procedure
Assuming that you have created your search profile (i.e. where, you can then apply the Tail search function to all the log files in that profile. To do this:
-
Select the profile containing the log files you wish to tail.
-
Click the + icon to open a new search tab.
-
Select the Tail option as the search Type.
-
Select the type of search parameter from the drop down box (for Tail only Text parameters are allowed).
-
Enter your search text.
-
If required, activate the Case sensitive check box.
-
Click the Start Tail button.
The resulting screen will show the last, most recent, log entries containing the search term you specified.
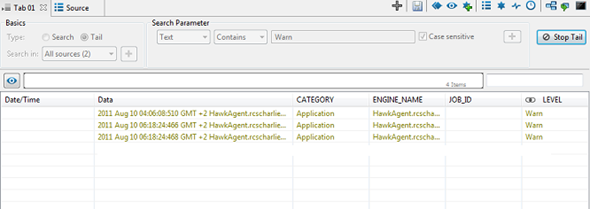
Tailing the suspect
As long as the Tail function is active, any newly generated messages containing the search text you entered will appear in the list as soon as it is logged, as shown in the following screen. You can always view the details of an entry in the list by clicking on it. The details are then displayed in a panel below the entry list (the Detailed Data Display panel), with your search term high-lighted, as shown in the following screen:
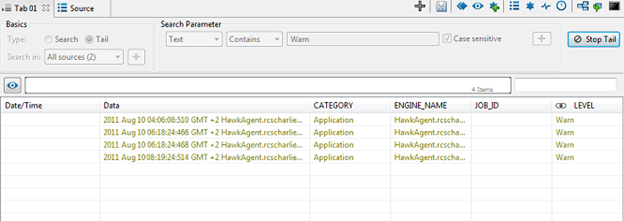
You can interrupt the tailing of a profile at anytime just by clicking the Stop Tail button. It is then possible to change your search text or restart the tailing for the same search parameters simply by clicking the Start Tail button again.
Section Heading Proin
Having set up the tails for the logs you want to monitor, you can now use Retrospective’s Disjoin Tab or Explode Window feature of the tabbed user interface to open the tabs containing your tails in separate windows. To disjoin a tab, simply drag and drop the desired tab outside the Retrospective window. To explode all open tabs into separate windows, click the icon or use the [Ctrl] + [E] keys in combination. Every tab is then replaced with a separate window and the screen will be divided to as many equal parts as the number of the tabs that were opened.
Whichever method chosen, the result is you are provided with multiple, always visible, real-time windows on the current state of the devices whose logs you are monitoring. This means you are now able to not only track threats after the fact, but catch them as they are happening. This access to real-time information during the identification phase of an incident handling procedure is what makes Retrospective’s Tail feature such a powerful tool for network analysis, maintenance and security.